The kernel, a computer program nestled at the heart of an operating system, commands everything within the system. Loaded into RAM right at the startup, it kick-starts other processes, managing the system's operations. However, not all processes are created equal, nor do they enjoy the same liberties within the system. This is where the concept of kernel rings comes into play, deciding the privileges and access rights of different processes through a structured hierarchy.
Kernel vs. User Modes: A Fundamental Distinction
At the core of this hierarchy are two primary modes: Kernel-Mode and User-Mode.
The following table highlights the fundamental differences between Kernel-Mode and User-Mode, illustrating how they balance efficiency, security, and system stability.
| Aspect | Kernel-Mode | User-Mode |
|---|---|---|
| Access to Hardware | Full access to all hardware and system resources. | Limited access; cannot directly access hardware or critical system resources. |
| Privileges | Higher privileges, allowing the execution of any CPU instruction and direct manipulation of memory. | Lower privileges, restricted to a subset of CPU instructions and memory areas. |
| Purpose | Used for executing critical system code that requires direct and unrestricted access to hardware and system resources. | Used for executing user applications and processes, providing a safer, more controlled environment. |
| Security Risks | A bug or security vulnerability can compromise the entire system. | Processes are isolated from the system core, reducing the risk of system-wide compromise. |
| Performance | Can operate more efficiently due to unrestricted access, but errors can lead to system instability. | Slightly less efficient due to additional checks and balances, but safer for system stability. |
| Examples | Device drivers, system services, kernel extensions. | User applications, such as web browsers, office software, and games. |
The Necessity of Multiple Kernel Rings
The basic setup of having Kernel and User Modes helps keep computers safe, but because computers do a lot of complex tasks, we need an even better way to keep things safe and running smoothly. This is where we use different levels of access, kind of like having different security clearances.
Think of device drivers, which are programs that let the computer talk to hardware like printers and keyboards. These drivers need to do more than what regular apps can, but letting them do anything they want could be risky. If something goes wrong with a driver, it could mess up the whole computer.
To avoid this, operating systems use a system with several layers, or "rings," of access. This way, drivers and other programs get enough access to do their jobs without getting the keys to the entire system. It’s like having a safety net that keeps small problems from turning into big disasters.
The Role of Kernel Rings in System Security and Stability
By implementing multiple rings of operation, the system can finely tune the access rights of different processes. This multi-tiered approach enhances security by ensuring that only the most trusted, critical components of the operating system operate with full privileges. Simultaneously, it bolsters system stability by isolating less critical components, reducing the risk that a fault in one area could lead to widespread system failure.
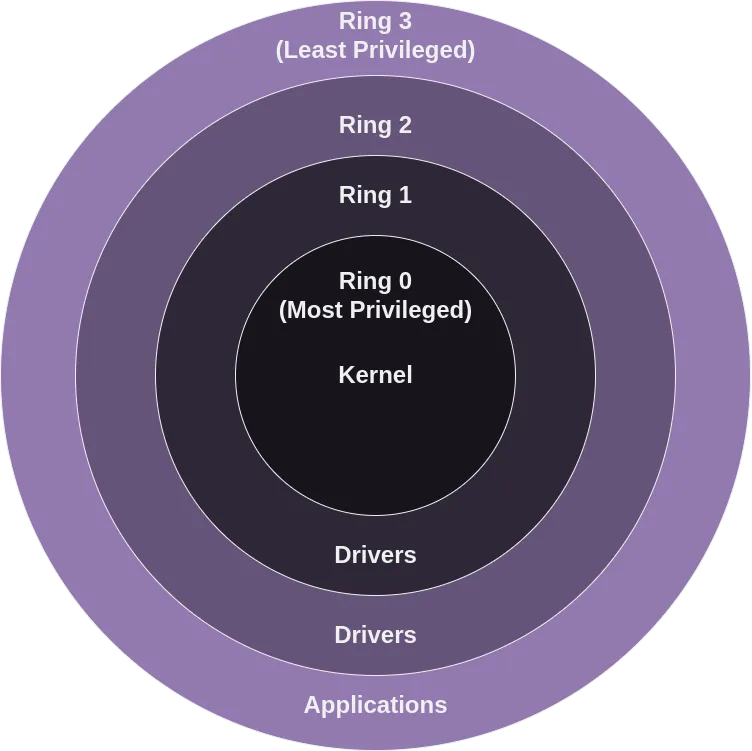
In essence, the architecture of kernel rings embodies the principle of least privilege, a cornerstone of modern computer security. By restricting processes to the minimum level of access necessary for their function, the system minimizes potential vectors for attack and error, safeguarding both the data and the overall integrity of the operating system.
In conclusion, the kernel and its associated rings represent more than just a technical necessity; they are the guardians of the operating system's security and stability. Through careful management of privileges and access, they ensure that the system remains both powerful and protected, capable of performing its myriad tasks while defending against both internal errors and external threats.









